Cyber Security Services
Recx offers a range of both bespoke and structured services, some of which are detailed below. We work closely with our customers to understand their needs and project requirements before creating a custom package of work. These can be half day briefings through to multi-month research engagements. Let us help you get the most out of your people and technology.
Vulnerability Research
Software and hardware often present an unknown risk within a organisation. Often products are mandated or can't be removed and as such understanding the potential exposure they present is key to structuring a defensive controls. Recx have strong experience inspecting products, reverse engineering, looking for vulnerabilities and where they're found looking to determine their potential.
If you have products in your organisation which present an unknown risk, we can perform detailed analysis and act as liaison with the vendor to establish an accurate risk picture and an effective defensive stance.
Product Evaluations
Selecting security products is a minefield. Every company claims that theirs is the best product and the perfect fit for your security and business needs. However our experience has shown that independent evaluation during the buying cycle can cut through marketing claims and ensure new security solutions don't contribute to your security problems by introducing unknown risks.
Recx have extensive experience of reviewing security products as part of a due-diligence process. Verifying claims, mapping attack surfaces and intensively inspecting and instrumenting software products. We work within your evaluation window, providing you with detailed analysis. Our service is designed to provide you with the information with which to make the most informed choice about how best to protect your business assets.
Security Assessments
Recx has considerable experience in performing application security assessments, at all stages of the development life cycle and using all major technologies and languages from C applications in embedded real time systems through to enterprise Java running in the cloud.
We've moved away from doing traditional black-box security assessments, believing them to be inefficient, ineffective and not representative of actual attacker capability. In order for Recx to offer the most value to our clients, while ensuring efficient and accurate results delivery, we've found working closely with both the application source code and the developers gives the greatest customer return. We can work within both waterfall and agile development models and if desired submit any security issues directly into a bug tracking system.

"We have always found Recx consultants to be very professional, highly knowledgeable and technical experts." - HMG Client
"Recx took the mystery out of penetration testing; they reviewed our sensitive assets and assisted us in successfully delivering risk assessments and audits to our security-conscious clients." - Healix International Limited
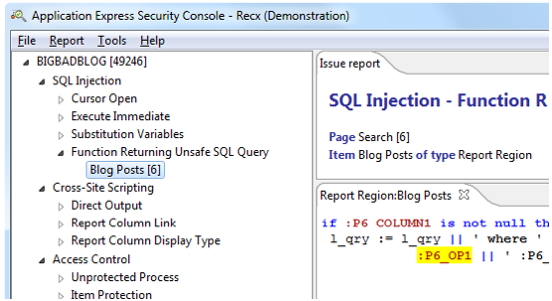
ApexSec - Oracle APEX Security
Our ApexSec Desktop product secures your APEX applications by scanning the source code looking for vulnerabilities. It is ideally used during the development life cycle and during QA testing.
ApexSec can help you quickly identify weaknesses in your applications without the specific knowledge of a security expert. We're proud to say that ApexSec is today used by Oracle as well as both commercial and Government customers as part of their application security process. More information...
"We would like to recognise and thank Recx Ltd. for the use of their ApexSec analysis engine, which has been used to improve the security of Oracle Application Express..." - Oracle
"ApexSec has already paid for itself!" - Lead developer, British Army
"Recx is in another league when it comes to APEX security, what I learned blew my mind, ecstatic to be partnering with them!" - APEX Freelancer
About Recx
Over several years the concept of a small, agile, British security company had been conceived between the founders but it wasn't until late 2009 that Recx was finally born. Created to provide our combined experience in the fields of system and network defence, attack, exploitation and application security research to both public and private organisations.
Our blend of skills comes from real world experience of compromising and defending the technologies and networks developed and utilised by central Government, the military, law enforcement, financial services, telecommunications and software companies. Recx is perfectly placed to provide valuable capability, insight, intelligence and creativity to the challenges faced by twenty-first century computing security.
James

James is one of founders of Recx and has been working in the field of computer security since being recruited in 2000, by DERA, an agency of the Ministry of Defence. For more than 21 years, James has combined cutting edge defensive and offensive security research with delivery of security consulting for leading private and public sector clients.
Nathan

Nathan has worked exclusively within the computer security arena for 25 years in various technical roles within both Government and UK commercial organisations. Prior to this Nathan was a developer involved with the production of commercial grade applications. He has performed incident response, computer forensics and countless penetration tests for a wide range of top UK and US businesses.
Tim

After graduating from Edinburgh University in 2000, Tim conducted advanced research in tandem with DERA's penetration testing team. By monitoring the developments of the growing computer security community, while validating and advancing research he enhanced the wider team capability through education and development of attack tools and techniques. Subsequently Tim has worked in research and consulting roles for QinetiQ, DSTL, Logica and SureCloud.
"Thanks a lot for the report, it gave us all the information needed to challenge our R&D." - Ipanema Technologies
In addition to the experience gained from attacking and defending technologies, Recx also has a strong pedigree in applied security research. This pedigree comes from individuals who have worked for organisations such as DERA, QinetiQ, DSTL, @stake, Symantec and Logica, performing research into both offensive and defensive technologies and techniques.
Working for their respective commercial or Government organisations and consulting into hundreds of others, the members of Recx have created and researched an extensive range of tools and techniques that assist in the defence and exploitation of computer systems and networks. Some of these are held privately and used to help our customers get the best out of their environments, others are offered as both free and commercial products.
"We really enjoyed working with Recx on the mobile music project, the feedback was clear and concise and easy to follow." - Abstraktion
Contact Recx
Recx Ltd. is registered in England and Wales as a private limited company (company no. 7100978).
VAT registration number: GB100686541.
Recx Ltd.
18/22 Church Street
Malvern
Worcestershire
WR14 2AY